Discord is a communication platform for video gamers. It advertises minimal CPU usage, high voice quality and multiple social media features like friend lists. As part of their communication platform, Discord has corresponding iOS and Android apps.
As a gaming enthusiast myself (Broodwar & SC2 forever!) and DFIR practitioner, there was plenty of motivation to see how this app stores user generated data in Android.
Test Devices and User Generated Data
The following testing devices were used:
- Samsung GSM SM-G530T Galaxy Grand Prime
- OS 5.1.1
- Privileged Access (root): Yes
- Samsung SGH-I747 Samsung Galaxy S3
- OS 4.1.2
- Privileged access (root): Yes
Using the same wireless network connection, the Discord app was downloaded and installed on the test phones. Two Discord accounts were created, one for each phone.
To create data for the app to store, I sent the following messages and pictures from one phone to the other using Discord. I also made a short VOIP call in the same manner. Oh and emoticons, of course.
For this analysis I wanted both free and paid for tools. It goes without saying that paid for tools come with customer support and ease of use that might not be available on a free or open source tool. Still a lack of funding for tools shouldn't be an obstacle to engage in meaningful forensic case work. Ideally an examiner will leverage all the tools at her disposal to paint the most complete picture possible.
The following software was used for forensic imaging:
The following software was used for forensic imaging:
Processing Tools
In order to read the imaged file system/s and for the parsing of artifacts the following tools were used:
- Cellebrite Physical Analyzer (PA)
- Autopsy 4
- FTK Imager 3.4.2.2
Both PA and Autopsy present the file system and parsed artifacts on the left of the screen and the related data on the panes to the right.
Analysis
PA presents the parsed chat artifacts it knows how to handle automatically under the 'Analyzed Data' section on the left pane of the PA screen. No chats were automatically parsed for Discord.
With PA it is always good to check the Installed Apps section. One is able to tell which apps are parsed by Cellebrite and which ones are not. Notice that next to the Discord line, under the 'Decoded by' heading there is no entry. If it were parsed by PA it would say 'Cellebrite' and a corresponding entry would have been found under the Chats section. Conveniently the app description itself tells us it is a chat application. The entries in the Installed apps section are pulled by PA from the 'localappstate.db' and the 'AndroidManifest.xml' files as seen in the screenshot below.
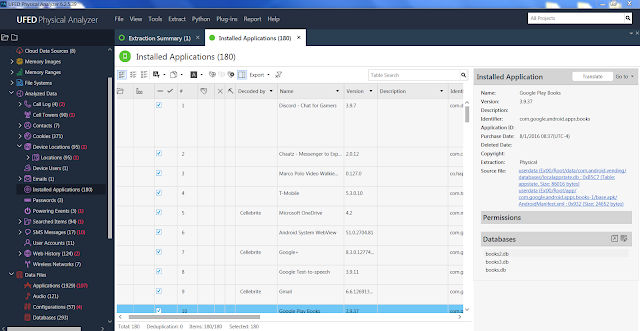 |
| Physical Analyzer - Installed Applications |
By contrast Autopsy does not parse the installed applications in order to present it in a spreadsheet as PA does. A manual search of the file system is needed to identify apps and data stores of interest. In most cases Android apps' data stores can be found in the 'userdata(ExtX)/Root/data/' directory. That being said, Autopsy does parse text messages and many other Android artifacts. In this particular instance both PA and Autopsy do not parse Discord artifacts automatically. The lesson to be learned is the value of manually traversing the acquired file system to make sure nothing is being missed no matter what tool is being used.
Within the data stores a directory for Discord was found.
 |
| Physical Analyzer - Discord App File Structure |
Within the 'userdata (ExtX)/Root/data/com.discord/files' directory multiple files with the 'PREF_K' prefix were located. For this analysis we will review the following:
PREF_K_STORE_MESSAGES_CACHE_V15
PREF_K_STORE_USERS_MAP_V7
PREF_K_STORE_USERS_ME_V7,
The PREF_K_STORE_MESSAGES_CACHE_V15 file contained the test messages that were sent.
PREF_K_STORE_MESSAGES_CACHE_V15
PREF_K_STORE_USERS_MAP_V7
PREF_K_STORE_USERS_ME_V7,
The PREF_K_STORE_MESSAGES_CACHE_V15 file contained the test messages that were sent.
 |
| Autopsy 4 - Indexed Text View |
It seems the file, which has no extension, calls some java functions first then below it stores the messages. In my experience most chat apps keep their messages in sqlite databases. In this instance no sqlite databases were found within the Discord directory. It would seem to me that these java related files are the data stores for the app itself. This assumption does require further validation. Note that both the messages and the usernames are missing the last letter as presented by the tools. For example the username 'spotmusic' is presented in the indexed text view as 'spotmusi' and the 'hello spot' message is presented as 'hello spo'.
For this test three pictures were sent. Two URL paths for every sent picture are contained within the message data store file. Here is an example.
 |
| Discord - Shared Media Paths |
'userdata (ExtX)/Root/data/com.discord/cache/app_images_cache_small/v2.ols100.1folder.'
The images have an internal naming convention and end with the '.cnt' extension. Autopsy recognizes them under the 'Extension Mismatch Detected' section under 'Extracted Content'.
 |
| Autopsy 4 - Extension Mismatch Detected |
By looking at the data store file, patterns seem to emerge. Further validation is still required.
For messages the following entries appear in the following order:
- Username missing the last letter.
- Message missing the last letter.
- Time of message.
For a VOIP call:
- Username missing the last letter.
- Call header
- Time
- Username missing last letter
- Time
 |
| FTK Imager - Call entry |
For an attachment:
- Attachment header (for the first image)
- Attachment name missing last letter
- URL #1
- URL #2
- User
- Time value
 |
| FTK Imager - Attachments |
For a pinned messages:
- Username missing last letter
- Unknown value, might denote pinned message
- Time value
 |
| FTK Imager - Pinned Message |
The PREF_K_STORE_USERS_MAP_V7 file denotes the individuals involved in the chat.
 |
| Autopsy 4 - Users Map |
The PREF_K_STORE_USERS_ME_V7 stores the username of the logged in user.
 |
| Autopsy 4 - Users_ME |
Conclusions
Truly no one tool can provide by itself a complete picture of what user activity transpired in a particular device of interest. Further testing and validation can reveal additional artifacts of interest regarding this particular app. There are estimates that indicate that Discord has approximately 25 million users.
By using paid for commercial tools as well as open source ones, the point is made that progress can be made regarding case work without the need of a bottomless budget.

