Discord on the desktop
In previous posts I discussed some ways of recovering and presenting Discord app chats from Android devices. This post will discuss how to find Discord chats in Windows machines and provide a simple way to visualize them.
As way of background Discord is a chat application whose target audience is people who play video games.
Wikipedia states that the Discord app has 87 million unique users. With such a large user base it is interesting to find that current commercial tools do not parse Discord chat artifacts directly yet.
Location and Extraction
Like many Windows applications, the user generated files and configurations reside in the apps folder. For example:
C:\Users\SampleUser\AppData\Roaming\discord
The Discord AppData folder has the following structure:
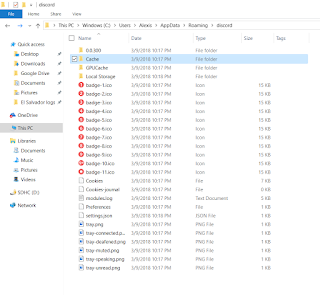 |
| Cache folder highlighted |
The user activity files are located in the Cache folder. At first glance the chat files we are looking for are not immediately apparent.
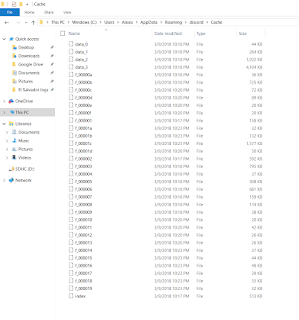 |
| Where are the chats? |
A look at the Cache folder contents might seem familiar. It is the same file format of the Google Chrome cache located at
C:\Users\SampleUser\AppData\Local\Google\Chrome\User Data\Default\Cache
My default browser is Chrome and the Discord app uses the same storage structure. For comparison here is my Chrome cache folder view.
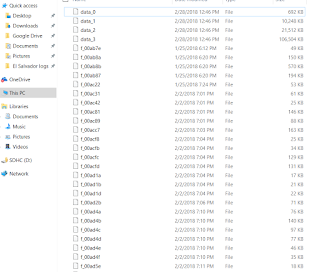 |
| Same file structure |
Since the file structures are the same it seem clear that the content we are looking for had to reside within the Chrome cache like folder structures in the Discord cache folder. Thankfully there are many tools that allow us to parse those structures and extract files from them. For this analysis I used the folowing tool:
The tool will by default parse the Chrome cache at the default folder location in your computer. Just hit stop on the upper left corner and point the tool to the Discord cache folder. After processing the contents of the folder the tool will show something similar to the following:
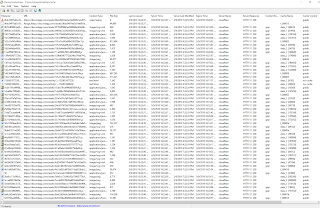 |
| Discord cache folder contents |
The tool will allow you to print out all the metadata on screen to an HTML file. Even more useful is the ability to extract the actual files from the cache by selecting an entry in the list and pressing F4 (or via the menu.)
To find the chat files look in the URL column for addresses that end with "messages?limit=50".
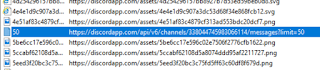 |
| messages?limit=50 |
These are the files we will export from the cache and will contain the chat messages. It is of note that they not always end in 50. In some cases they can end in 100. Also note that the name of these files is usually 50 as stated in the URL variable but that is no always the case. Some chat names start with the words After or Before followed by some sort of numeric ID. Hence the best way to identify them is to go by the ending of the URL column.
By clicking on file entry in the list one can see the pertinent metadata. It states that the files we are exporting are JSON files.
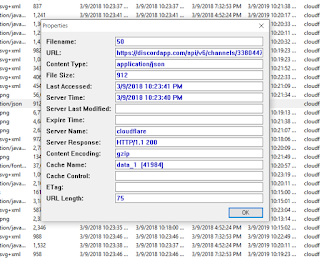 |
| Content Type: application/json |
Since they are JSON files they can be viewed in any regular file viewer. After exporting here is how one looks using Wordpad.
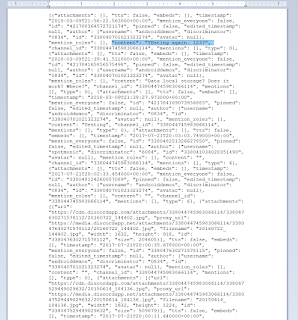 |
| Content key is key |
The formatting is hard to the eyes but understandable. Notice the content key, the value is the user generated chat. Each user generated block starts with the attachment key and continues with keys for multiple time stamps, user IDs, the chat content and the like.
In order to make it a little easier to read the values, the following script takes the json file contents and presents them as a collection of html tables.
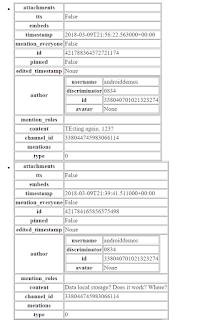 |
| A little better |
The best way to look at these files is to use Chrome since other browsers do not know how to decode certain characters, like emoji.
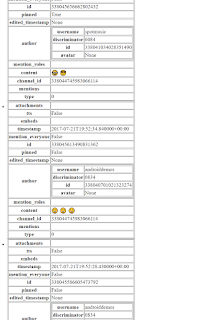 |
| Look!!! Emojis!!! |
The script is really simple and can be found here:
Script uses the json2html module that does the actual heavy lifting. It can be found here:
Pending will be the capability for the script to parse a group of chats in a folder instead of one by one.
PD:
One can log into a target Discord account without the username and password by installing the Discord application on our forensic computer and then copying over the Discord app data folders from the examined computer. The program will require internet access for this to work. It goes without saying that consent to search or a search warrant is needed before attempting this type of access.
-Brigs





















