CCleaner for Android keeps application usage related data in the following location:
data/data/com.piriform.ccleaner/databases/The following queries at https://github.com/abrignoni/DFIR-SQL-Query-Repo can be used as templates to extract information from the CCleaner SQLite databases.
- Scheduled cleans.
- Usage stats.
- Aggregate list of installed apps to include deleted apps.
- Apps identified via a CCleaner scan with corresponding last scan timestamps.
- Emulated storage media filename list from selected directories.
CCleaner installation and first usage timestamps can be found in the following XML file:
com.google.android.gms.measurement.prefs.xmlThe XML file is located at:
data/com.piriform.ccleaner/shared_prefs/
Long version
Mobile extractions can provide different degrees of visibility into what type of artifacts can be gleaned from the device under examination. For example in most instances a physical dump will enable us to get at more artifacts than an Android backup extraction would. In situations where the extraction at hand provides limited visibility we can look at extracted apps to complement our view.
CCleaner for Android is a well known app with over 50 million downloads.
The app is advertised as a simple way of reclaiming storage space and speeding up the device.
When the app is accessed, and the Analyze button is pressed, it presents bar graphic stating that a scan is in progress. When the bar gets completely filled a list of apps and related directories that can cleaned by emptying their corresponding cache folders is shown. It looks as so:
The list is divided in the following categories:
Notice the scan time in the image. The Flud application was not available on my sample Android backup extraction. I would have not known the device had the application installed at some point since my extraction was not able to pull the usual files used to determine installed applications (like packages.xml). The only way I found to replicate such behavior in CCleaner is to deleted an app with the Android uninstall function, as opposed to using CCleaner itself to make the uninstall, while also making sure that the deleted app did not have any associated directories in the emulated storage directory.
When the app is accessed, and the Analyze button is pressed, it presents bar graphic stating that a scan is in progress. When the bar gets completely filled a list of apps and related directories that can cleaned by emptying their corresponding cache folders is shown. It looks as so:
 |
| Apps after scanning |
- Hidden cache
- Visible cache
- Empty folders
- Downloads
When the FINISH CLEANING button at the end is pressed the app presents how much space was saved.
 |
| Saved space. |
Running the scan a second time the app list is shorter than the first go around.
 |
| Fewer apps. |
By looking at the data/data/com.piriform.ccleaner/databases/ directory one sees that the database which contains the scanned app data is properly called scanner-cache.db. This database lists apps that have data in the /data/data/ and related /data/media/ directories. When a scan is responsive to any of those directories the package name and the timestamp is added to the scanner-cache.db in the appInfoCache table. Based on my testing the timestamps in the database will correspond to the latest scan of the apps and directories, hence why all the timestamps are separated at most by milliseconds. Is there an exception to the rule?
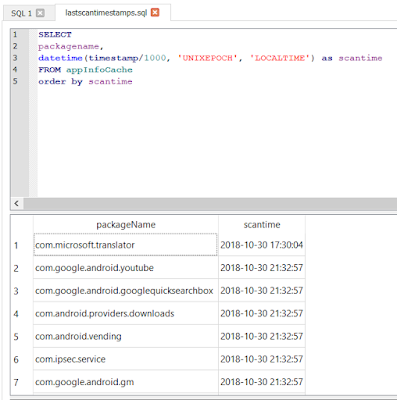
In the following image I sorted the contents of the database by timestamp. Notice the first entry.
 |
| Odd man out. |
Notice the scan time in the image. The Flud application was not available on my sample Android backup extraction. I would have not known the device had the application installed at some point since my extraction was not able to pull the usual files used to determine installed applications (like packages.xml). The only way I found to replicate such behavior in CCleaner is to deleted an app with the Android uninstall function, as opposed to using CCleaner itself to make the uninstall, while also making sure that the deleted app did not have any associated directories in the emulated storage directory.
 |
| Odd man out. |
What does this tell us? Not only does the list tells us what installed applications were at some point scanned by CCleaner but it can also gives us a time range of when the odd man out app, scan time wise, was deleted. In the first image the Flud app was deleted at some point between 2018-09-24 08:00:00 and 2018-10-10 17:51:33. In the second image the Translator app was deleted at some point between 2018-10-30 17:30:04 and 2018-10-30 21:32:57.
With this information the next steps would be to see if any other artifacts for Flud or Translator exist on the extractions under examination. For example in the case of Flud you might want to start looking for media player history files that include the application path for Flud downloads. As a popular BitTorrent client many individuals use it to download multimedia files. A media player that accesses such paths might retain the paths and filenames of media viewed from Flud directories even if those directories are not present in the extraction.
Can apps that have never been downloaded and/or installed be on this list? I have not seen this to be the case for obvious reasons. Can deleted apps still be found on the list that have a last/current scan time? Yes! And this is why testing and validation is so important. To assume that all the apps in the list were present/installed at the most current scan time could lead us to make an unsupported statement. My current hypothesis on why deleted apps might still have the most current scan times resides on the fact that these apps have related directories in emulated storage or in another location on the device. My limited tests seem to support the hypothesis but further testing is needed to confirm.
Another CCleaner file of interest is the com.piriform.cleaner.db database. It contains automated scheduled cleans.
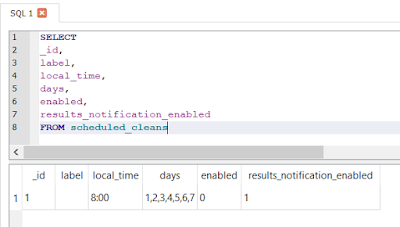 |
| Schedule your cleans. |
I have not found this database in a free CCleaner app installation.
The cleaner_apps_db contents seem to match a list of installed apps. I have seen deleted apps persist in this database.
 |
A list of CCleaner usage stats can be found in the cleaner database.
 |
| Usage stats |
Items that start with SAFEC are generated when an Analyze and Clean option is selected. Items that start with ADVC_CLEARED are generated when a Analyze and Clean Memory option is selected. The statistics are grouped by day and do not contain details on what was deleted.
A list of media filenames in emulated storage can be found in the myroll database.
 |
| Media list in emulated storage. Notice the was_deleted column. |
Installation and first use CCleaner timestamps can be found in the com.google.android.gms.measurement.prefs.xml file located at data/com.piriform.ccleaner/shared_prefs/.
Conclusion
Conclusion
Third-party apps can augment our visibility into device artifacts when we are working with extractions that have limited file or system information. Testing and validation keep being of paramount importance since any conclusions we reach need to be supported by evidence and not only hunch or opinion.
Since information that is not shared is information that is lost, these SQL queries are now accessible at the DFIR SQL query repository.
https://github.com/abrignoni/DFIR-SQL-Query-Repo/tree/master/Android/CCLEANER
As always I can be reached on twitter @alexisbrignoni and email 4n6[at]abrignoni[dot]com.
As always I can be reached on twitter @alexisbrignoni and email 4n6[at]abrignoni[dot]com.
