On my second post I received great feed back from Sarah Edwards. She pointed me to the contents of the mobile installation logs in iOS.
 |
| Cool stuff! |
 |
| I'll do it. |
https://github.com/abrignoni/iOS-Mobile-Installation-Logs-Parser
These logs contain a lot of information. Currently the script only extracts the following events:
- App install successful with date and time.
- App container made live with date, time, and path.
- App container moved with date, time, and path..
- App destroying container with date, time, and path.
Here is a sample screen of how the logs look as taken from the device. The image has been zoomed out which could make it harder to read unless the preview image is clicked.
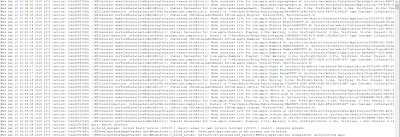 |
| Lots of data. |
The script is really simple to use.
- Have Python 3.6.4 or newer installed.
- Extract the logs from the /private/var/installd/Library/Logs/MobileInstallation/ directory.
- Place the script in the same directory as the extracted logs.
- Execute the script via CMD.
The screen, after done, should look something like this:
 |
| Run complete. Some stats. |
The script will produce one SQLite database called mib.db, a directory named Apps_State, and a directory named Apps_Historical.
 |
| Script with generated items. |
The SQLite database holds the extracted information from the lines of log data. The script queries the database to produce the contents within the two directories.
The Apps_State directory can have two files within it. These are named InstalledApps.txt and UninstalledApps.txt. The contents reflect the name of the text files. Here is a sample image of InstalledApps.txt content:
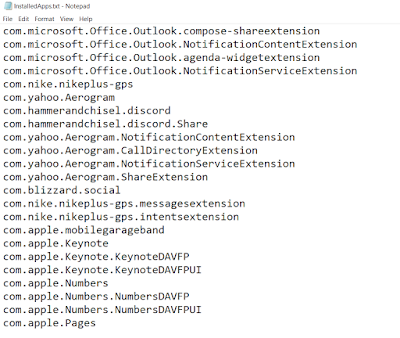 |
| List of installed apps. |
Having this list handy is really useful since it can be used to compare the currently installed apps within the file system image that might have been missed by our third party forensic tool of choice.
If one would like more context in regards to when the app was installed and where the app directory is located the Apps_Historical directory has all that information per app.
 |
| A txt file for every app. |
Here is a sample of the historical information regarding an installed app.
 |
| Historical events for com.blizzard.social |
Notice the report has a timestamp for every event. The scrip puts the most recent events at the top so the current path for the application directory can be at or near the top.
Here is a sample of historical information regarding an uninstalled app.
 |
| Historical event for org.videolan.vlc-ios |
Like the previous report there is a timestamp for every entry and events start with the most recent at the top. These report are useful if one wants to determine when an app was uninstalled or if a current app was uninstalled and then reinstalled multiple times.
 |
| Historical events for org.coolstar.electra1131 |
Notice the multiple 'Destroying', 'Made', and 'Install Successful' entries in the report. Again the most recent ones are at the top.
As seen above the script's output is responsive to the original requests of installed apps with corresponding app directory paths. It goes further by identifying uninstalled apps and by providing timestamps and historical app event aggregation.
By looking at the logs there seems to be further areas where the script can be improved. This is my soon to-do list:
- Report on 'detected reboot' and other log entries that indicate system state as opposed to particular app states.
- Add 'updated bundle entries' for 'container made live' context in the historical reports.
- Add 'attempting delta patch update' and app version information in the historical reports.
- Add 'uninstall requested' and 'uninstalling identifier' in the historical reports.
I can't thank enough my colleague @i_am_the_gia for testing out the script on her data sets and Sarah Edwards for making me aware of the logs.
If anyone gives the logs a look and finds further items to report on or wants to give other feedback I can, as always, be reached on twitter @alexisbrignoni and email 4n6[at]abrignoni[dot]com.