Discord for iOS keeps chat data in the following directories and files:
- /private/var/mobile/Containers/Data/Application/*UUID*/Library/Caches/com.hammerandchisel.discord/fsCachedData/
- The UUID formatted directory name in the path maps to the bundle id of the app.
- Chat and media files found in the fsCachedData directory.
- All chat content in JSON format.
- /private/var/mobile/Library/FrontBoard/applicationState.db
- SQLite database.
- Contains a bplist that establishes the relationship between the bundle id (com.hammerandchisel.discord), app id (Discord.app) and the UUID folder name in the Applications folder.
- Look for app name in 'application_identifier_tab' table. Take id number. Use id to extract blob field in the 'kvs' table. Open blob to map UUID to application name.
- The more direct way to determine the correct application folder where the data resides is to open each one by one and look for the bundle id in the path or by using commercial tools.
- /private/var/mobile/Containers/Data/Application/*UUID*/Documents/RCTAsyncLocalStorage_V1/manifest.json
- Key value pairs in JSON format.
- Contains items like 'LAST_VIEWED_PATH', 'first_run_date_key', and 'Emoji UsageHistory.'
Long version:
This post is a continuation of the Discord digital forensic analysis on all platforms that it is available. The main purpose is to determine where user generated items are located like chats and related multimedia files. Discord is supported on browsers and multiple operating systems.
 |
| Supported platforms |
So far I have reviewed Discord in the following platforms:
- Finding Discord app chats in Windows
- Discord Android app review DFIR
- Discord Android app - Missing values not missing
- Finding Discord chats is OS X
- Discord JSON chats to HTML/XLS
This blog post will discuss Discord in iOS devices.
Testing Platform
For analysis I am using the following device and equipment:
Acquisition
My first attempt to extract Discord data from the device involved using Magnet Forensics Acquire and Cellebrite Physical Analyzer. None of the available extraction methods provided user generated Discord data. iTunes backup was also not aggregating any Discord files. The only solution was to try and jailbreaking the device in order to access the file system. The instructions I followed for the jailbreak came from the ElcomSoft blog here. It worked.
It is of note that even though the device was jailbroken the extraction/imaging tools at my disposal did not recognize the device as such. My assumption is that the current version of the Apple File Conduit is not compatible with the jailbreak being used. Thankfully it was fairly easy to extract the file system data via SSH connection from the iPhone to the forensic workstation SIFT virtual machine. Sarah Edwards in her 'Getting Saucy with APFS' presentation explains how to make a tarball of the iPhone file system via SSH. It worked like a charm. All done in a single line.
ssh root@iphoneip -p 22 'tar -cf - /private/var' > data.tar
After decompressing the tar bundle the logical files where processed with Autopsy and Cellebrite Physical Analyzer. No user generated Discord artifacts were present in the tools' parsed artifacts sections.
Analysis
There are multiple ways of navigating the acquired logical files in order to find Discord data. The most basic one is to do an index/text/keyword search for the term 'Discord.'
Another option is to navigate to the
Commercial tools can establish this association for you.
See the field application id, identifier and the source file for these values in Physical Analyzer. Since one of the plists with the required information resides in the directory we are trying to identify to begin with this method did not seem to be the fastest way to go when a manual examination is being done or when using an open source tool like Autopsy.
/private/var/mobile/Containers/Data/Applicationdirectory and look through the UUID named folders for the one that corresponds to the Discord app.
Commercial tools can establish this association for you.
 |
| Cellebrite Physical Analyzer |
My approach:
Looked for the Discord app bundle id and search for that specific term within the data. There are various ways to obtain this bundle id. For this analysis I searched for the bundle id in a lookup web page here. For the Discord app the bundle id is 'com.hammerandchisel.discord'.
 |
| https://offcornerdev.com/bundleid.html |
The bundle id keyword search in Autopsy led me to the 'applicationState.db' file located at
/private/var/mobile/Library/FrontBoard/This SQLite database provided the connection between the bundle id and the UUID numbers in the 'Application' directory.
Open the SQLite database with a SQLite browser. Look for the bundle id name in the 'application_identifier_tab' table. Take note of the corresponding id number. In this instance it is 101.
 |
| Look at the id field with the 101 value. |
Use the 101 id and look for it in the 'kvs' table in the 'application_identifier' field . Export the blob in the value field for the id. The exported data is a bplist that maps all pertinent UUID numbers to the application name and/or bundle id. The data can also be seen in the preview pane in binary mode without the need to export the blob content.
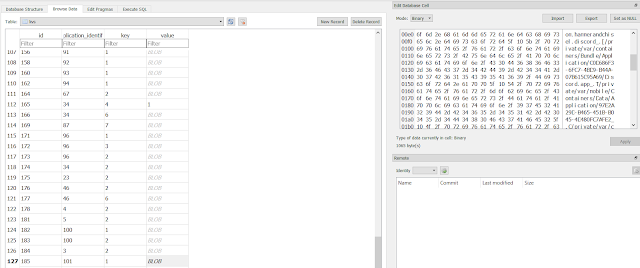 |
| Blob as binary data |
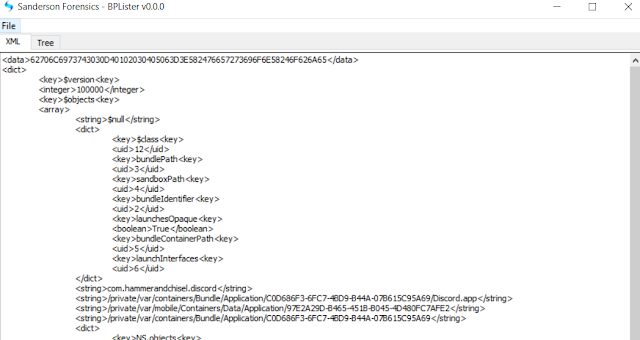 |
| These are the UUIDs we are looking for. |
The user data Discord directory per the bplist in my test device was the following:
/private/var/mobile/Containers/Data/Application/97E2A29D-B465-451B-B045-4D480FC7AFE2/ |
After finding the proper UUID named folder for Discord, here is the file structure for it:
 |
| Notice 'fsCachedData' right under 'com.hammerandchisel.discord' |
Chats and media
The chats were located in the following directory:
/private/var/mobile/Containers/Data/Application/*UUID*/Library/Caches/com.hammerandchisel.discord/fsCachedData/The chats are in the expected JSON format.
 |
| Chat data in JSON |
 |
| JSON to HTML/XLS conversion |
https://github.com/abrignoni/Discord-JSON-chat-conversionsHere is a sample of how the JSON chat looks in HTML format:
 |
| Truncated for better viewing |
 |
| Easy to see the content quickly. Even emojis!!!! |
 |
| We got media too. UUID like names. |
/private/var/mobile/Containers/Data/Application/*UUID*/Documents/RCTAsyncLocalStorage_V1/manifest.json
 |
| Image truncated for visibility. |
Be it via a jailbroken phone or alternate extractions that provide access to the iOS file system, knowing how and where to look for pertinent artifacts can be just as important as the extraction of the file system itself. Hopefully the paths, files and methodology here can speed up Discord artifact examinations.
I plan on taking a look at Discord for Linux soon. This will close out all platform analysis for the Discord service.
As always I can be reached on twitter @alexisbrignoni and email 4n6[at]abrignoni[dot]com.
Thanks!
