The LA Fitness app for Android is an example of how a non messaging application can have plenty of relevant data if only one cares to look.
- Gym check-ins: club name, date, time and location. Sample data covered a year's worth of check-ins.
- Pin code for the app.
- Billing information to include the last 4 digits of the credit card in use.
- Registration information: membership start date, name, address, phone, email, home club.
Long version
LA Fitness is a gym club with more than 700 locations across the United States and Canada. The Android app has more than a million downloads.
 |
| LA Fitness in the Google Play Store |
A lot of case work involves finding GPS coordinates, message content and media of interest. The app does not seem to have anything to do with the previous and still as a user I've notice that some of the information it shows me could be of relevance in a case. Is there information that it does not show me? What could it be?
Testing platform
Details of hardware and software used can be found here.
Extraction and processing
Magnet Forensics Acquire - Full physical extraction.
Autopsy 4.8.0
Analysis
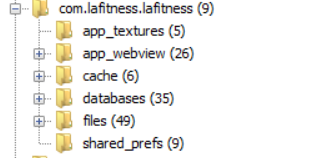
The LA Fitness app data folders can be found here:
Interestingly enough the relevant information resided in the files folder, not in databases. A look at the contents of databases folder shows that most SQLite files seem to manage data related to multimedia files and menus used by the app. None seem to track any user generated requests or actions. More testing needed of course.
From the files directory I identified four files containing user related content.
1. Gym check-ins
GYM-NAME - Street address
XX/XX/XXXX 00:00:00 AM/PM
The GYM-NAME is the same as the city where the facility is located.
In my sample data the check-ins go back as far as a year.
2. Pin code for app access
3. Billing information
It is of note that if the billing name can be different from the name on top. It also keeps the last 4 digits of the credit card number.
4. Customer information
Conclusion
From the Android third party video player database that contained proof of file access to the gym application that had the pin code needed to access a previously out of reach data store, new data can be found when and where we least expect it. As examiners it is true that our time is short and the cases plenty but to be at our most effective we need to think more about how we can streamline our workflows. Lately I've been getting great results from parsing my mobile extractions with Autopsy for fast index searching within SQLite databases while making it a habit of going through the databases section in Physical Analyzer looking at non-decoded data stores. As part of this streamlining of processes I will review in the next blog post the new Virtual Analyzer by Cellebrite.
As always I can be reached on twitter @alexisbrignoni and email 4n6[at]abrignoni[dot]com.
/userdata/data/com.lafitness.lafitness/
Interestingly enough the relevant information resided in the files folder, not in databases. A look at the contents of databases folder shows that most SQLite files seem to manage data related to multimedia files and menus used by the app. None seem to track any user generated requests or actions. More testing needed of course.
From the files directory I identified four files containing user related content.
1. Gym check-ins
/userdata/data/com.lafitness.lafitness/files/MembershipCheckinsData is formatted as:
GYM-NAME - Street address
XX/XX/XXXX 00:00:00 AM/PM
The GYM-NAME is the same as the city where the facility is located.
In my sample data the check-ins go back as far as a year.
2. Pin code for app access
/userdata/data/com.lafitness.lafitness/files/4-digitpinUsed for a screen app lock. Cleartext file.
3. Billing information
/userdata/data/com.lafitness.lafitness/files/AccountProfile
It is of note that if the billing name can be different from the name on top. It also keeps the last 4 digits of the credit card number.
4. Customer information
/userdata/data/com.lafitness.lafitness/files/AccountProfileSame fields as billing information with the addition of a few extra fields regarding the type of access the client has to gym services like personal training, guest passes and premium status.
Conclusion
From the Android third party video player database that contained proof of file access to the gym application that had the pin code needed to access a previously out of reach data store, new data can be found when and where we least expect it. As examiners it is true that our time is short and the cases plenty but to be at our most effective we need to think more about how we can streamline our workflows. Lately I've been getting great results from parsing my mobile extractions with Autopsy for fast index searching within SQLite databases while making it a habit of going through the databases section in Physical Analyzer looking at non-decoded data stores. As part of this streamlining of processes I will review in the next blog post the new Virtual Analyzer by Cellebrite.
As always I can be reached on twitter @alexisbrignoni and email 4n6[at]abrignoni[dot]com.